Author: James Weakley
We’d like to introduce James Weakley, a Data Architect at nib health funds, who recently wrote a short blog post on the topic of KNIME Server and Okta. James has given us permission to republish it here. But first a few words about James.

James' role at nib is to support data analytics practice from a technology perspective. This involves guidance on how to best leverage cloud products for performance elasticity, as well as operationalizing through integration with other business applications.
nib’s BI analysts seek to understand and predict customer behavior, and recently started using KNIME Server to assist with this, and so that they could better leverage the Snowflake data warehouse in a team environment.
As James rightly points out in his post below, KNIME Server Large supports LDAP out of the box (full documentation is available here); it’s also possible to set up Kerberos Single sign-on as well, but the really nice thing about the Okta setup, is that two-factor auth comes almost for free! The other very convenient aspect is that the whole KNIME Server deployment is handled on AWS. In case that is something that interests you, there is plenty more information here. And finally, as you can see in the ‘shout outs’ at the end of his article, it was great to see that our trusted partners at Forest Grove Technology were able to help James along the way.
"Okta have built a successful company on making authentication easy, and recently their managed LDAP interface became generally available to all customers.
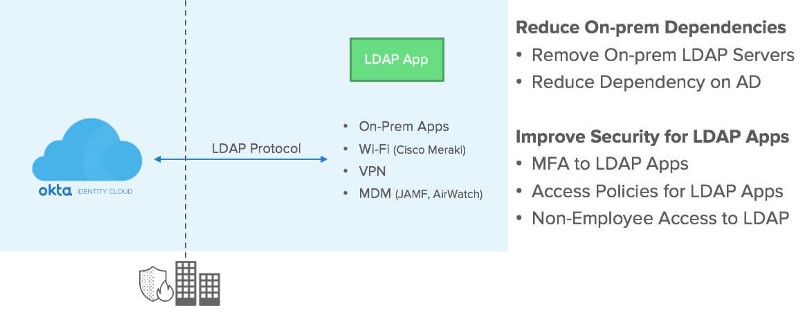
It was great timing for me, as I was helping out our Business Intelligence team deploying KNIME Server to our AWS environment. KNIME Server is the commercial complement to the open source KNIME Analytics Platform. In line with the analytics software industry’s undying love of Java, it runs on Apache TomEE.
LDAP is a supported method of authentication for KNIME Server. Let’s face it, 99% of the time in an enterprise scenario, this involves pointing it at a Microsoft Active Directory domain controller.
An Okta customer can instead point it at their Okta LDAP interface. For example, if your Okta domain is your_org.okta.com, in your server.xml file you would define a Realm like this:
The connection password is passed in as an environment variable using the CATALINA_OPTS section of setenv.sh. In our case, we retrieve this value from AWS Systems Manager Agent (AWS SSM) at boot time.
Importantly, I extended the LDAP connection timeout to 60 seconds, from the default of 5 seconds. This is because in the Multi Factor Auth(MFA) scenario, Okta waits for the MFA acknowledgement by the user, before responding to the LDAP request.
Finally, you have to tell KNIME which LDAP group the KNIME admins belong to. This is done in the knime-server.config file under the workflow repository directory.
Here I am at the login screen:

When I click “Login”, my iPhone immediately buzzes me to approve the login in the Okta Verify app, while the browser waits:
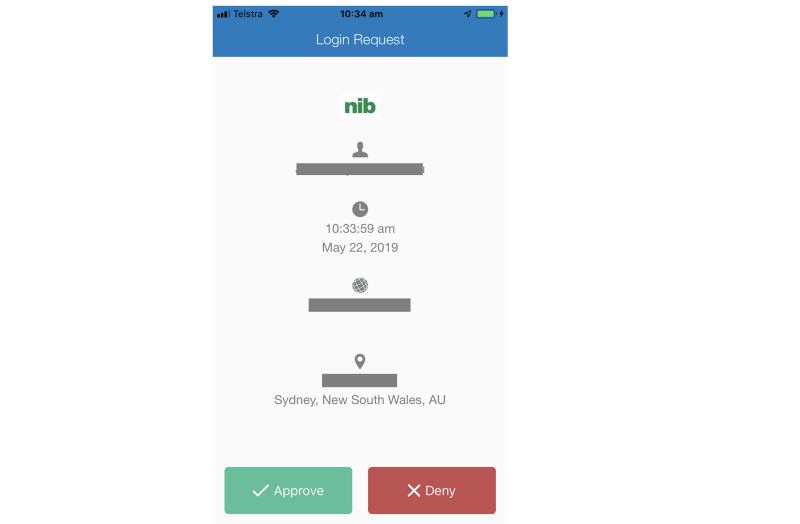
Once I click Approve, I'm in!
Shout-outs to Luke Gibson (nib’s resident Okta guru) and Forest Grove Technology for helping out along the way with this deployment."
As first published on Medium
Useful links
Check out the first four videos in a series on KNIME Server, just released on Friday!
